Are you looking to fix your database’s performance and safeguard your data? Database consulting pinpoints weak spots and strategizes enhancements tailored to your business’s unique demands. This article breaks down the transformative impact of consulting services, helping you to navigate the intricacies of database optimization and security.
Database Consulting Key Takeaways
- Premier database consulting services offer comprehensive solutions to optimize database performance and security, providing tailored assessments, tuning, migration support, and architecture design aligned with business goals.
- Performance and security of databases are enhanced through expert techniques, including query optimization, monitoring tools, applying best practices, and implementing high availability and disaster recovery solutions.
- Real-world success stories highlight the tangible benefits of database consulting services in performance improvement and security enhancement, showcasing significant operational upgrades and bolstered defenses against cyber threats.
Unlock the Potential of Your Database Systems
Your database systems are critical to your business.
Database consulting services can help businesses maximize the potential of their database systems, leading to increased efficiency, productivity, and informed decision-making. Database consultants offer a comprehensive solution to optimize database environments and improve performance, utilizing innovative techniques and professional knowledge. Trust in their expertise to achieve success and reach your business goals.
Whether it’s database performance, database engine migration, or other improvements you’re after, database experts can provide tailored solutions addressing your specific database needs. Expert database consultants are crucial to unlocking your database’s potential; they bring proficiency in databases from multiple platforms (Mysql, SQL server, Postgres, Singlestore), ensuring your database runs smoothly and efficiently.
Comprehensive Consulting Services
Effective database management hinges on comprehensive consulting services. These services encompass various tasks, from conducting audits and assessments, planning and designing the database architecture, and even facilitating upgrades and migrations. Each of these consulting engagements is crafted to deliver practical expertise in commercial database management, providing tailored solutions to meet each client’s unique needs and objectives.
The role of these services extends beyond simple consultancy. They are instrumental in:
- Enhancing database performance tuning
- Conducting evaluations of existing database infrastructure
- Identifying optimization opportunities
- Addressing database problems
- Enhancing database security
- Conducting thorough data security assessments
- Offering insights and recommendations to secure databases at an enterprise level
These services ensure a seamless customer experience, providing crucial information and support at a fixed fee, making them an asset to any organization.
Expertise in Mysql, SQL Server, and Other Platforms
The SQL Server is a commercial DBMS known for its strong performance, scalability, and intuitive interface. Its distinctive qualities make it an excellent option for organizations needing a reliable DBMS with efficient permission management. However, the success of your database system is not solely determined by the platform you choose; it also relies heavily on the expertise of your database consultants.
Enhancing Database Performance
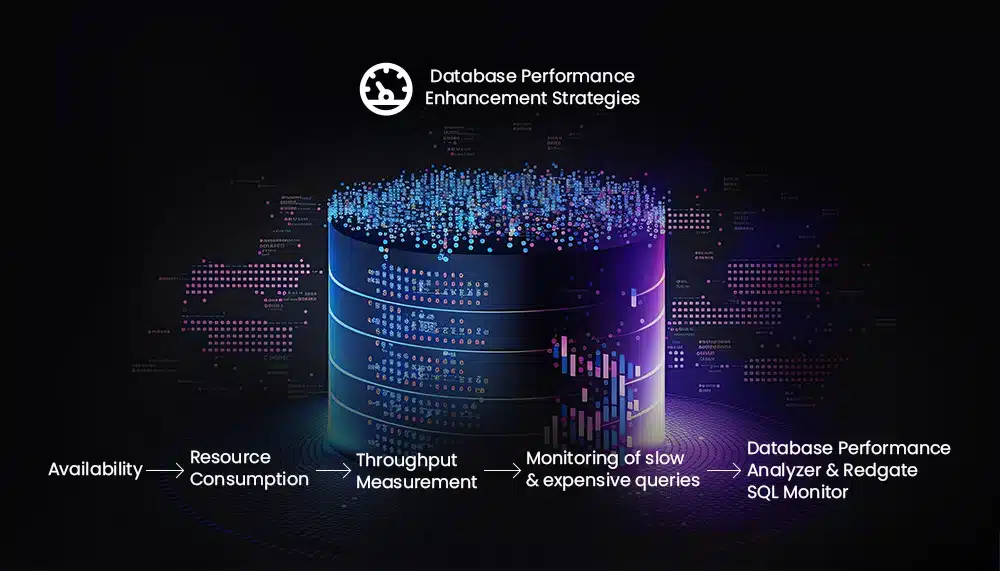
Once your database system is in production and shows high CPU usage, higher database storage cost, and an increase in application latency, the next action is performance enhancement.
Performance is the heartbeat of your database, with every beat representing a transaction, a query, or a data retrieval operation. It’s about ensuring that your database is not just functioning but functioning at its best. This is where performance tuning techniques come into play, providing the necessary tweaks and adjustments to optimize your database’s efficiency.
Enhancing database performance is contingent upon meticulous tracking of:
- Availability
- Resource consumption
- Throughput measurement
- Monitoring of slow and expensive queries
With the right tools, such as Database Performance Analyzer and Redgate SQL Monitor, you can effectively monitor and fine-tune your database performance, ensuring optimal operation at all times.
Performance Tuning Techniques
Database consultants utilize performance-tuning techniques as their primary tools to optimize efficiency. These techniques include:
- Query optimization
- Data defragmentation
- Increasing memory
- Overhauling CPU
- Improving indexes
- Upgrading the database
These techniques aim to re-optimize the system from a software and hardware perspective, resulting in accelerated query response and improved index performance.
The implementation of these techniques can yield significant efficiency gains. Your database system operates at its optimum level by increasing memory allocation, enhancing query response times, and maximizing application performance. Furthermore, consistent monitoring and tuning of the system can enhance workload scalability through performance improvement and reduction of database load. This ensures your database is running smoothly and aligns with your business expansion and efficiency objectives.
Monitoring and Best Practices
While performance tuning techniques bolster your database’s efficiency, monitoring and best practices ensure ongoing performance improvements and proactive issue resolution. This proactive approach to database management involves the following:
- Keeping track of schema updates
- Using database logging
- Measuring key metrics
- Automating monitoring processes
- Logging and archiving relevant events
Implementing routine database monitoring can lead to performance improvements by ensuring the continuous online availability of databases, identifying optimal SQL for tuning, and analyzing performance metrics to pinpoint and address bottlenecks. In addition, proactive measures can be taken to resolve common database issues, such as analyzing logs to gain insight into the issue, optimizing database performance based on log analysis, proactively monitoring database metrics to detect issues early, and frequently assessing critical data assets.
With these strategies in place, you can confidently navigate database management challenges and maximize performance.
Strengthening Database Security
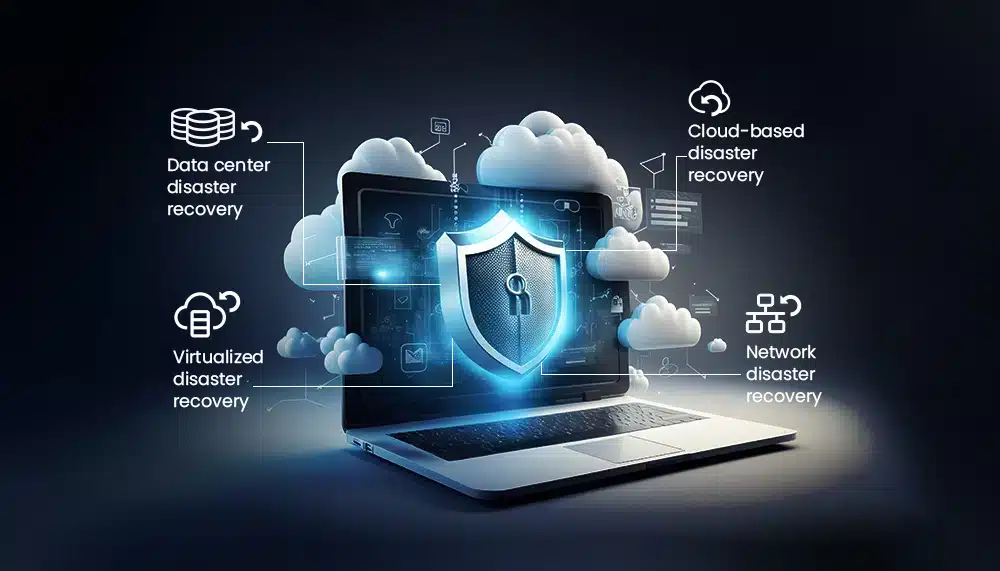
In today’s digital landscape, fraught with data breaches and cyber-attacks, strengthening database security is a priority for every organization. A robust security strategy protects your critical data, ensures regulatory compliance, and maintains customer trust. With the right approach, you can enhance your database security by segregating database and web servers, encryption of data at rest and in transit, enforcement of robust authentication, and regular software updates.
Enhancing database security also means preparing for the worst-case scenario – a disaster. Implementing effective disaster recovery solutions can ensure business continuity in the face of unexpected events. Some options to consider are:
- Data center disaster recovery
- Network disaster recovery
- Virtualized disaster recovery
- Cloud-based disaster recovery
Coupled with high availability solutions, which guarantee uninterrupted operation of the database system, you can preserve access to essential data and applications, even in the most challenging circumstances.
Security Assessment and Recommendations
Any effective security strategy rests on the foundation of a comprehensive security assessment. This process involves:
- Performing security testing before database deployment
- Checking for default, blank, and weak username/passwords
- Assessing for the likelihood of SQL injections
- Managing user access rights
- Monitoring user activity
The outcome of this process is a clear understanding of your database’s security posture and a roadmap for improvement.
The vulnerabilities identified during a security assessment can range from SQL injections to weak passwords, excessive user privileges, and broken databases. Addressing these vulnerabilities requires a combination of best practices, including deploying physical database security, segregating database servers, setting up an HTTPS proxy server, avoiding default network ports, and continuously monitoring and auditing database activity. With these measures, you can improve your database’s security posture and protect your valuable data assets.
Disaster Recovery and High Availability Solutions
Disaster recovery is critical in guaranteeing business continuity by reinstating data access and IT infrastructure post-disaster. Whether it’s a natural disaster, a cyber-attack, or a simple human error, having a solid disaster recovery plan can mean the difference between a minor inconvenience and a major business crisis.
Effective disaster recovery solutions for database security include:
- Data center disaster recovery
- Network disaster recovery
- Virtualized disaster recovery
- Cloud-based disaster recovery
- Disaster Recovery as a Service (DRaaS)
In addition to disaster recovery, high availability solutions play a significant role in enhancing database security by implementing mechanisms that guarantee uninterrupted operation of the database system. Implementing high availability for database systems may include synchronous cluster replication, which may introduce latency due to two-phase commits, or redundancy and isolation strategies to ensure continuous operation and minimize the impact of downtime.
With these solutions in place, you can rest assured that your data is always accessible, even in adversity.
Streamlining Database Migration and Transformation
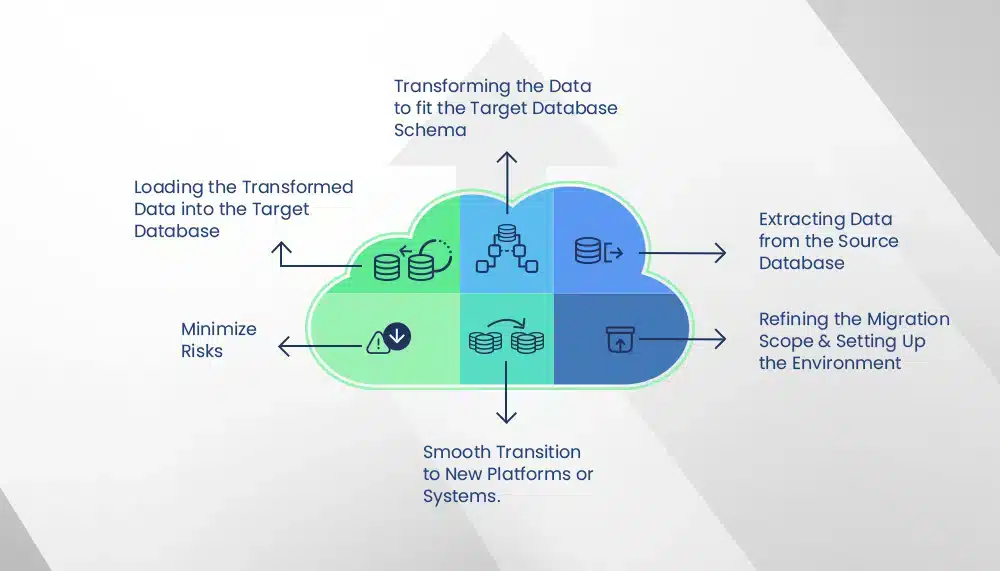
The evolution of your database must follow that of your business. Whether it’s to leverage the latest advancements in database technology, enhance functionality, or ensure compatibility with new software and systems, database migration and transformation are often necessary steps in maintaining a high-performing database system. However, these processes can be complex and fraught with challenges. This is where premier database consulting services come in, providing the expertise and resources to streamline the process, minimize risks, and ensure a smooth transition to new platforms or systems.
Database migration and transformation is a multi-step journey, including the following steps:
- Refining the migration scope and setting up the environment
- Extracting data from the source database
- Transforming the data to fit the target database schema
- Loading the transformed data into the target database
Each step can present challenges like data loss, semantics errors, extended downtime, and data corruption. But with expert guidance and meticulous planning, these challenges can be effectively managed, ensuring a successful migration.
Migration Planning and Execution
The database migration process relies heavily on the critical phase of migration planning and execution. It involves the following steps:
- Refining the migration scope
- Assessing the source and target systems
- Setting up the migration environment
- Extracting, transforming, and loading data
- Validating the migration
- Replicating the process as needed
Each step requires careful consideration and planning, with potential risks including data loss, semantic errors, downtime, data corruption, and application performance issues.
Minimizing downtime during a database migration is a key concern for many organizations. To address this, it’s crucial to assess migration readiness, determine essential data for migration, and consider approaches such as offline copy migration or a master/read replica switch strategy. The migration process can be smooth and efficient with the right tools, such as Microsoft SQL Server Integration Services (SSIS), Oracle Data Integrator, Hevo Data, and Fivetran.
Post-Migration Support and Optimization
The completion of migration doesn’t signal the end of work. Post-migration support and optimization are crucial to ensuring the continued success of your database system. This involves:
- Implementing cost management and optimization strategies
- Reconciling data accuracy
- Identifying performance issues
- Monitoring cloud spending
These measures can help ensure that your database continues operating at its best, even after the migration.
Optimization is a continuous process that is no different after a database migration. Post-migration optimization involves implementing recommended optimizations to enhance data-layer performance, fine-tuning performance, reducing latency, and addressing performance issues. With the right tools, such as:
- AWS Database Migration Service
- Microsoft SQL Server Migration Assistant
- Oracle Data Migration
- Informatica PowerCenter
- Talend
- SAP Data
- DBConvert Studio
You can continue to optimize your current database and maximize performance.
Customized Database Architecture Design
Just as every business is unique, so should its database architecture. A customized database architecture is specifically designed to meet your organization or application’s distinct needs and demands. It involves:
- Establishing a database structure
- Defining relationships between data entities
- Enhancing performance and security in line with your system’s unique characteristics.
Aligning your database architecture with your business goals can provide a strategic advantage, enabling:
- High visibility and transparency of information to all employees
- Integration of IT infrastructure with business objectives
- Aiding top management in comprehending the value of data and its strategic utilization for the company.
In addition, a flexible and scalable architecture allows for easy scaling based on load, handling large amounts of data, cost-effectiveness, and flexibility in adapting to changing business needs.
Aligning with Business Goals
Database architecture, when well-designed, aligns seamlessly with your business goals. It can:
- Ensure high visibility and transparency of information to all employees
- Integrate IT infrastructure with business objectives
- Aid top management in comprehending the value of data and its strategic utilization for the company
By following these principles, your database can become a strategic asset that drives your business forward.
The process of aligning your database architecture with your business objectives involves:
- Assessing the current state
- Defining the desired outcomes
- Thoroughly understanding the business’s goals and objectives
- Comprehending the current state of the architecture
- Identifying any gaps and opportunities
This approach ensures that your database supports your business goals rather than hindering them.
Scalability and Flexibility
A successful database architecture necessitates scalability and flexibility. Scalability ensures that your database can handle increased workloads without requiring a complete overhaul, while flexibility allows easy adaptation to changing business needs.
Designing a database architecture with scalability and flexibility in mind can present several challenges, such as poor performance, data integrity concerns, security vulnerabilities, and the need for a highly available data-intensive architecture. However, overcoming these challenges can provide a range of benefits, from cost savings and improved performance to exploring new markets and maintaining competitiveness.
Real-World Success Stories
Real-world success stories paint the actual value of premier database consulting services. These stories provide tangible proof of the improvements that can be achieved in database performance and security through these services. Whether it’s a logistics company’s tracking system operating on a SQL Server or companies like Microsoft, Verizon, and the Pokemon Company enhancing their database security, these success stories testify to the transformative power of expert database consulting services.
These success stories don’t just showcase the benefits of database consulting services, they also highlight the importance of best practices in database management. These practices are at the heart of every successful database project, from performance tuning and monitoring to implementing robust security measures and disaster recovery solutions. By following these practices, businesses can improve their database performance and security, achieve their business goals, and enhance the customer experience.
Performance Improvement
Database performance improvement emerges as one of the key benefits of database consulting services. A case in point is the logistics company’s tracking system, which operates on a SQL Server. Significant improvements were made in the effectiveness and speed of database operations through expert intervention, showcasing the value of performance tuning and monitoring.
Implementing professional tuning and monitoring has resulted in measurable improvements in database performance, utilizing tools and methods that facilitate the assessment and documentation of efficiency enhancements and reductions in response time. By implementing the recommended best practices, these businesses have improved their database efficiency and ensured high availability and scalability, benefiting their overall operations.
Security Enhancement
Enhancing database security is a top business priority in an era of frequent data breaches. Companies like Microsoft, Verizon, and the Pokemon Company have successfully improved their database security by leveraging Dell’s Cyber Recovery Solution, using cloud migration to improve data protection, and implementing DevSecOps practices. These measures have protected their critical data and provided them with a competitive advantage, reduced development costs, and prevented hacking attempts.
Implementing disaster recovery solutions has further improved database security, ensuring the security and reliability of systems and implementing data protection, backup, and recovery processes to mitigate security risks. With these measures in place, these businesses have safeguarded their data and ensured business continuity, demonstrating the value of robust database security measures.
Summary
In conclusion, premier database consulting services provide a comprehensive solution to enhancing the performance and security of your database systems. From unlocking the potential of your database and improving performance to strengthening security and streamlining migration, these services offer a pathway to data-driven success. Armed with expert knowledge and innovative techniques, you can leverage the full potential of your database, drive your business forward, and stay ahead of the competition. So, are you ready to transform your database operations and propel your business to new heights?
Frequently Asked Questions
What does a database consultant do?
A database consultant is a highly qualified IT professional who assists businesses with choosing, maintaining, and customizing computer database management and information systems and helping to migrate to newer DB solutions on the market. This includes implementing databases, testing changes, and evaluating information storage requirements.
How can database consulting services enhance my database system?
Database consulting services can enhance your database system by providing expertise in identifying key data sets, building secure environments, and ensuring smooth operations. They also offer comprehensive services such as audits, architecture planning, and upgrades.
What measures can I take to strengthen my database security?
Segregate your database and web servers, encrypt data at rest and in transit, enforce robust authentication, and regularly update your database software. Additionally, consider implementing effective disaster recovery and high-availability solutions for business continuity.
How can I design a customized database architecture that aligns with my business goals?
Assess your current state, define desired outcomes, and understand your business goals and current architecture to design a customized database aligned with your business objectives. Focus on scalability and flexibility for cost savings, improved performance, and maintaining competitiveness.







