Snowflake password-only access is officially being deprecated for all user accounts. This important update requires organizations to move beyond traditional username-and-password logins to stronger, more secure authentication methods.
In this guide, we’ll go over everything that’s changing, why it matters, and how your company can smoothly transition to these enhanced security standards designed to protect sensitive data and maintain compliance.
What Is Changing in Snowflake Authentication?
Snowflake is implementing a major security policy update, which is the deprecation of password-only access—logins without any secondary verification. These authentication methods were very common due to their simplicity, but they’re becoming increasingly insufficient in protecting sensitive data.
With the Snowflake password deprecation, organizations must replace static passwords with more secure mechanisms to prevent unauthorized access and comply with evolving security standards. This means that users will no longer be able to authenticate using only their username and password, as they previously could.

Instead, all accounts must transition to stronger authentication methods, such as multi-factor authentication (MFA), single sign-on (SSO), or federated identity solutions. This involves a phased approach, and Snowflake has announced the change and encouraged administrators to begin migrating away from password-only logins.
Snowflake will also announce a future enforcement date, which will mark the point at which accounts relying exclusively on password-only login won’t be able to sign in. Additionally, those who haven’t migrated by the cutoff date risk losing access until alternative authentication is configured.
This is an important Snowflake security update that requires immediate attention, especially for enterprise accounts, because delaying migration can lead to operational disruptions, security vulnerabilities, and non-compliance issues. Thus, it’s very important to act ahead of Snowflake password depreciation enforcement to ensure a smoother transition to new authentication mechanisms.
Why Snowflake Is Moving Away from Password-Only Access
Snowflake’s decision to deprecate password-only access stems from a growing need to protect sensitive data from increasingly sophisticated cyber threats. Password-only access was the cornerstone of digital authentication. Over time, however, such authentication mechanisms have become one of the most exploited vulnerabilities in modern cloud environments.
Snowflake is a platform that handles massive volumes of enterprise data across finance, healthcare, and retail, and relies solely on password-only authorization, which is no longer sufficient to ensure data security or regulatory compliance.
It’s a reasonable shift, because password-only access is susceptible to several well-documented risks. Phishing campaigns can deceive users into disclosing credentials, while brute-force and credential stuffing attacks leverage automated tools to exploit weak or reused passwords.
Insider threats, including shared credentials or unmanaged user accounts, also create additional exposure that’s difficult to track or remediate. These risks can translate into unauthorized access to sensitive data and potential breaches with massive financial, legal, and reputational repercussions.

The Snowflake security update also reflects a broader shift in industry standards towards enhancing security measures. Major cloud providers, such as AWS, Azure, and Google Cloud, have already moved to deprecate static credentials in favor of stronger, more secure authentication models, such as the aforementioned MFA, SSO, and federated identity solutions.
By adopting similar measures, Snowflake ensures its platform aligns with evolving best practices in enterprise data security, and switching to MFA or SSO not only addresses compliance requirements but also helps enterprises establish a more resilient and scalable approach to data security.
Beyond risk mitigation, there are also operational benefits of moving to MFA or SSO, like reduced administrative overhead, more seamless login experiences, and finer control over access policies without additional friction to workflows.
Overall, Snowflake’s decision is both a defensive measure against present threats and a proactive investment in scalable, future-proof security for its users.
What Authentication Methods Will Replace Passwords?
As previously mentioned, organizations will have to adopt stronger, more reliable, and standards-based authentication methods to maintain access now that Snowflake is phasing out password-only logins. The platform currently supports several secure options, each addressing different operational and compliance needs.
| Authentication Method: | Security Level: | Best For: | Complexity: |
| Multi-Factor Authentication (MFA) | Medium-High | Small to mid-sized teams without centralized identity systems | Low |
| Single Sign-On (SSO) | High | Enterprises using identity providers | Medium |
| Identity Federation | Very High | Large enterprises with hybrid environment or complex role requirements | High |
The most commonly used replacements include the aforementioned MFA, SSO, and identity federation authentication mechanisms.
Multi-Factor Authentication
MFA adds an extra verification layer beyond the standard username and password. It typically involves a one-time passcode or hardware token. This method significantly reduces the risk of account compromise, even if the primary credentials are exposed.

Snowflake supports time-based one-time passwords (TOTP) and can integrate with common MFA providers. This is a great option for smaller teams and environments that don’t have centralized identity systems, as they present a cost-effective improvement in security without significant changes to the existing architecture.
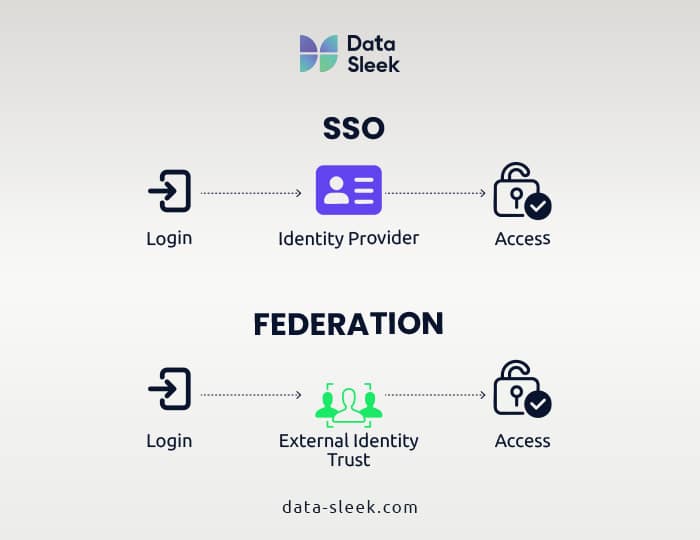
Single Sign-On (SSO)
SSO allows users to authenticate to Snowflake using an existing corporate entity provider, such as Microsoft Entra ID (formerly known as Azure AD), Okta, or Google Workspace. This approach centralizes user management and provides seamless access across multiple apps.
Implementing Snowflake SSO configuration simplifies lifecycle management by allowing administrators to control access directly from their identity providers. It’s a great option for organizations with strict compliance needs.
Identity Federation
Federated identity extends the SSO model by allowing Snowflake to trust credentials managed by an external identity system, without duplicating Snowflake’s own user records. This is especially suitable for larger entities or those with hybrid environments due to unified identity plane access.
Snowflake’s move fits into the broader trend of zero-trust architecture, where access is never implicitly granted, even within the network. By requiring identity verification via MFA or IdPs, Snowflake helps enterprises implement zero-trust more effectively.
How to Transition Your Snowflake Environment
Transitioning away from password-only authentication isn’t an easy task, and depending on the size of your enterprise, the transition might be phased. The process involves assessing current access methods, selecting a secure alternative to password-only authentication, and configuring that alternative with minimal disruptions.
Organizations that approach this transition systematically can use the deprecation as an opportunity to strengthen their overall identity management strategy, rather than just treating it as a purely reactive change.
Step 1—Assess Current Access Points
Begin by identifying which users and services are still using password-only authentication. This requires auditing Snowflake’s access logs and reviewing the existing identity management configurations. Look for accounts that haven’t been integrated with MFA, SSO, or federated identity, and prioritize their remediation.
Service accounts, automated scripts, and third-party integrations often rely on static credentials and are often overlooked during user-focused audits, so they demand special attention during transitions. Make sure that there’s nothing left behind, as even a single unmanaged credential can create a significant vulnerability.
Step 2—Choose Your New Authentication Method
Choosing the most suitable alternative is the next step, and for organizations that rely on identity providers like Okta, Microsoft Entra ID, or Google Workspace, Snowflake’s SSO configuration or identity federation may be ideal due to their centralized control.
Smaller teams without such infrastructures may prefer Snowflake’s MFA for its simpler implementation and immediate security benefits. In either case, the decision should align with broader IT policies. Also, engaging security teams early ensures the chosen method satisfies compliance and long-term strategic goals.
Step 3—Configure Your New Setup
Implementation involves configuring the chosen authentication method within Snowflake and, where applicable, the external identity provider. Snowflake’s documentation provides detailed instructions for setting up MFA, SSO, and federation, including role mappings and conditional access policies.
Testing at this stage is critical, and you should pilot the new setup with a subset of users to validate functionality, confirm role assignments, and ensure that workflows remain uninterrupted. Once validated, extend the configuration across all accounts and deprecate password-only credentials.
You should also maintain clear communication with users throughout the process to reduce confusion and prevent helpdesk overload during the cutover.
Configuration Tips and Best Practices for Smoother Transition
Migrating to MFA or SSO is actually quite straightforward in principle. In practice, the process is often challenging due to the complexities of enterprise identity systems. Still, you can ensure a smooth rollout and prevent major disruptions with proper planning and configuration.
The following tips address common hurdles and offer guidance for secure and efficient setup:
- Integrate with Existing Identity Providers—Configuring Snowflake SSO or identity federation through existing identity providers (which we mentioned previously) ensures consistent access policies across all corporate applications. It’s important to ensure that the mapping between the identity provider and Snowflake matches to prevent a mismatch during login, which could impact Snowflake access control.
- Prioritize MFA Enrollment Early—Organizations that use Snowflake’s MFA setup should encourage their users to enroll as early as possible. Of course, organizations should also provide clear instructions and support for configuring TOTP apps or hardware tokens. Early adoption will reduce last-minute support issues and ensure that the organization is fully prepped before password-only deprecation takes effect.
- Test Role Mapping and Access Policies—Test role mappings carefully to ensure users receive the correct permissions upon login when deploying SSO or federated identity. Incorrect mapping can lead to overprovisioning or restricted access, both of which create operational and security risks. This is why you should validate access in staging environments before applying organization-wide changes.
- Document and Communicate Changes—Snowflake authentication changes impact everyone, and documenting the new login process, as well as communicating timelines, enrollment steps, and support resources, minimizes confusion. Proactive outreach helps prevent spikes in support tickets during the transition and ensures compliance with regulations and security policies.
- Monitor and Adjust Post-Deployment—After rolling out MFA or SSO, monitor authentication logs to identify any anomalies or issues. Post-deployment adjustments, such as refining conditional access policies or updating MFA fallback methods, help maintain security without affecting productivity.
Security and Compliance Implications
Deprecating password-only access strengthens Snowflake’s alignment with modern compliance frameworks like SOC 2, HIPAA, and GDPR. These Standards increasingly view static passwords as insufficient for safeguarding sensitive data, so by adopting MFA, SSO, or federated identity, organizations not only reduce the risk of breaches but also demonstrate proactive compliance during audits.
Delaying migration carries both security and regulatory risks. Accounts that remain PW-only may become non-compliant and could potentially lead to audit findings and penalties. From a business perspective, this update is an opportunity to modernize Snowflake account security and embed stronger access controls that support ongoing regulatory obligations.
Common Pitfalls When Transitioning Snowflake Authentication
Even well-prepared teams can encounter challenges when moving away from password-only access. While Snowflake provides flexible and secure authentication options, successful implementation hinges on thorough planning and execution.
Recognizing common mistakes ahead of time can help your organization avoid disruptions, misconfigurations, and security gaps. One of the most frequently overlooked issues is failing to disable unused password-only accounts after the new system is in place. These legacy credentials remain a security risk if not fully decommissioned, even if they’re inactive.
Another pitfall is improper identity provider-to-role mapping. Misaligned roles can lead to overprovisioned access or incomplete login failures post-migration and post-integration with Okta, Workspace, or Entra ID. This is why it’s important to test role mapping with a limited user group in a staging environment before an organization-wide rollout.
Many teams also rush the rollout without proper piloting, especially when facing a compliance deadline. While speed is important, skipping internal testing increases the risk of disruptions, lockouts, or misapplied security policies. These common pitfalls can severely delay compliance with the Snowflake password deprecation and leave your data exposed.
To avoid these setbacks, it’s really important to document every step of the migration. You should also engage IT security teams early on, and treat the transition as both a technical upgrade and a change in management process.
How Data Sleek Can Help
Transitioning from password-only access can be quite challenging. Data Sleek offers expert consulting to help you optimize your Snowflake environment and implement secure authentication methods like MFA and SSO.
Whether you need strategy or hands-on support, Data Sleek provides expert consulting tooptimize your Snowflake environment and implement secure authentication methods tailored to your organization. Book a free consultation to explore our Snowflake consulting services and see how we can help you align with the Snowflake password deprecation requirements.


