Snowflake is ending password-only logins—here’s how to protect your data and avoid downtime. This guide discusses Snowflake authentication updates, why they matter, and how to prepare with a structured migration strategy that follows the best practices and long-term governance goals. So, without further ado, let’s dive in.
Understanding Snowflake’s Authentication Shift
Snowflake recently announced that it’s moving away from password-only authentication, in favor of stronger mechanisms, such as Multi-Factor Authentication (MFA) and federated Single Sign-On (SSO). This change is part of Snowflake’s broader strategy that addresses the increased number of credential threats, phishing, and automated attack techniques.
The move also mirrors what has already become standard across most enterprise SaaS and cloud data platforms. In short, Snowflake authentication changes are designed to eliminate one of the weakest links in modern cybersecurity: standalone passwords and password-only authorization.
And this shift isn’t without reason; password-only access has been recognized as one of the weakest forms of authentication due to its susceptibility to the aforementioned attack techniques and human error. By enforcing stronger authentication measures, such as MFA or SSO, Snowflake is actually following industry best practices and embracing the Zero Trust security model.
This approach minimizes the risk of compromised accounts while simplifying governance and auditability, which are critical priorities for enterprises that manage sensitive data. However, the change won’t be sudden, and Snowflake is rolling it out through a phased deprecation strategy.

While the exact timeline varies by account tier and region, the transition will begin with opt-in options and advisory notifications before moving to stricter enforcement. Enterprises that fail to act before full deprecation risk sudden access disruptions, which will adversely impact automated workflows.
Furthermore, data pipelines, reporting dashboards, and integrated applications that still rely on password-only authentication will fail, potentially leading to significant downtime and operational bottlenecks.
From a leadership perspective, this should be treated as part of a broader data security and compliance strategy, rather than a tactical “fix.” Changes are most effective when championed by leadership, and waiting until the last minute introduces unnecessary risks. Proactive planning, on the other hand, allows you to map your authentication model to your organizational priorities.
The key message here is that Snowflake’s login changes aren’t optional, and they can be leveraged to strengthen the entire data ecosystem if enterprises migrate to MFA or SSO authorization systems on time. Otherwise, you’re risking loss of access, administrative overhead, compliance issues, and massive workload disruptions.
Why Secure Authentication Matters More Than Ever for Data
The modern world relies on vast amounts of sensitive data, so the security of authentication systems is directly tied to the integrity and availability of business intelligence. Passwords alone are no longer adequate for protecting said sensitive data assets, particularly when platforms like Snowflake serve as central repositories for mission-critical information.
The risks of relying on outdated authentication mechanisms are well-documented, and stolen credentials are among the most common causes of data breaches, often due to weak or reused passwords and social engineering attacks.
By moving beyond password-only authentication, Snowflake is aligning with a broader industry recognition that identity is the new security parameter. Thus, the adoption of MFA and SSO isn’t simply about meeting regulatory requirements or ticking compliance boxes; it’s about operational resilience.
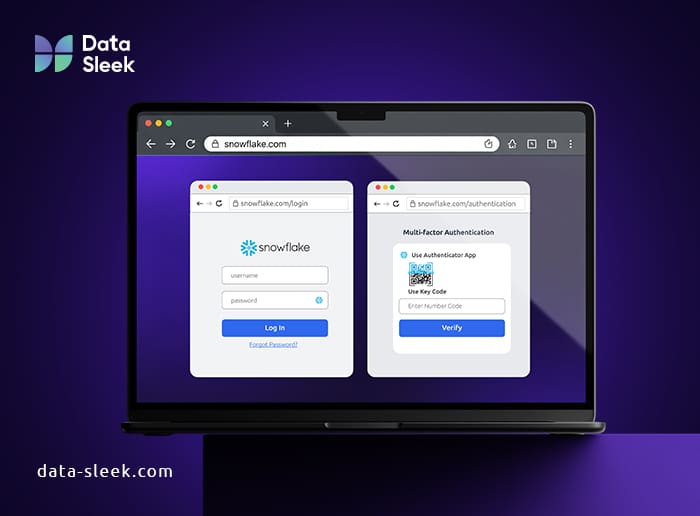
Multi-Factor Authentication adds a second layer of defense, as it requires users to verify their identity through time-based one-time passwords (TOTP) or hardware security keys. This drastically reduces the likelihood of unauthorized access, even if the primary credentials are compromised. It’s a good balance of enhanced security and minimal user friction.
SSO, on the other hand, delivers both security and efficiency at scale, which is why it’s the best option for mid-to-large enterprises. By integrating Snowflake with enterprise identity providers, such as Okta, Azure AD, or Ping Identity, businesses can centralize user access, apply consistent conditional policies, and eliminate the burden of managing different sets of credentials.
SSO also reduces help desk costs associated with password resets and improves the onboarding experience for new employees or contractors. For decision-makers, SSO is an investment in both security and operational efficiency, as it simplifies access management while maintaining tight control over identity governance.
Beyond technical advantages, these authentication mechanics also support broader compliance and governance objectives. Regulations such as SOC 2, HIPAA, and PCI DSS require auditable controls over data access, and MFA and SSO implementations make it easier to meet these standards while still providing detailed visibility into login activity.
Your Action Plan: Migrating to Enhanced Snowflake Authentication
Preparing for Snowflake’s authentication changes requires a bit more than simply toggling a new security feature. It demands a structured approach that introduces technical implementations without adversely affecting business operations.
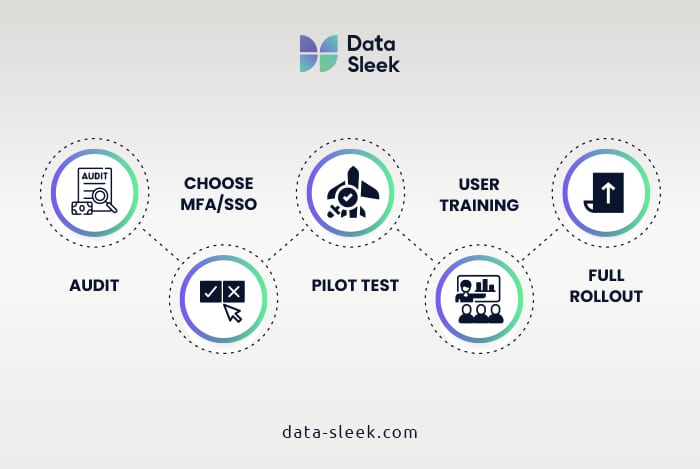
A successful migration involves auditing your current environment, selecting the right authentication method, and executing the transition with minimal disruptions to users and critical workflows. As previously mentioned, by treating this as a phased project rather than a last-minute patch, you can mitigate risks and avoid unplanned downtime.
Step 1: Assess Your Current Snowflake Authentication Setup
The first step towards a seamless transition is assessing the current state of your authentication setup and gaining complete visibility into how your organization authenticates to Snowflake. This involves identifying all users, roles, and automated services that rely on password-only logins.
Interactive users, such as analysts and developers, may be straightforward to identify, but automated connections, such as scripts, pipelines, and third-party integrations, tend to be overlooked. Thus, conducting a comprehensive audit will help you uncover dependencies that need to be addressed before password deprecation occurs.
Understanding use patterns and identifying potential points of friction is also very important. This insight can help guide the technical configuration and user training later in the process. You should also inventory any existing password reset procedures that should be retired or replaced with more secure mechanisms.
By gaining a clear understanding of your current authentication setup, you’ll be better equipped to choose the most appropriate authentication method for your organization.
Step 2: Choosing Your Preferred Authentication Method (MFA vs. SSO)
Authentication methods are not one-size-fits-all solutions, and the choice between MFA and SSO depends on the size of your organization, the complexity of your infrastructure, and your long-term identity management strategy. Both options enhance your security, but ultimately serve different operational needs. Here’s what you need to know:
| Feature | Multi-Factor Authentication (MFA) | Single Sign-On (SSO) |
| Primary Use Case | Human users, smaller teams | Enterprises with centralized identity |
| User Experience | Login with password + additional verification | One-click login via federated credentials |
| Setup Complexity | Low, native support in Snowflake | Medium, requires IdP (Okta, Azure AD, etc) |
| Centralized Policy Control | No | Yes |
| Scalability | Moderate | High |
| Admin Overhead | Higher (per-user setup) | Lower (centralized provisioning) |
| Fallback Options | SMS, app-based codes | SSO fallback login policies via IdP |
| Best For | Quick wins, low-barrier security upgrades | Scalable, policy-driven identity architecture |
- Multi-Factor Authentication—MFA introduces a second layer of verification that requires users to confirm their identity with something other than just their password. This is commonly done through an authenticator app, SMS code, or hardware tokens. Since Snowflake natively supports MFA, this authentication mechanism is the fastest way to comply with Snowflake’s password deprecation. And while it enhances your baseline security, sadly, it doesn’t centralize user management like SSO does. It’s also the fastest for human users, but service accounts and pipelines require special handling.
- Single Sign-On—SSO takes authentication to the next level by federating identity management across different systems. Integrating Snowflake with different identity providers allows users to log in using a single set of credentials governed by centralized policies. Snowflake SSO configuration is ideal for larger organizations, as it provides a unified point of control for access rules, while reducing the need for repeated logins and help desk password resets.
You should really consider the scale and maturity of your organization when deciding between MFA and SSO. Smaller businesses with fewer users and limited integrations are more likely to benefit more from enabling Snowflake’s MFA setup, as it’s often the quickest and most cost-effective solution.
However, for enterprises with complex ecosystems, SSO is a natural choice, as it offers better scalability, streamlined onboarding, and better alignment with identity management strategies. In many cases, organizations adopt a hybrid approach, with MFA acting as a short-term measure while planning and phasing an SSO implementation.
Need help navigating complex authentication setups? Our experts can help you choose and implement the right solution for your data needs.
Step 3: Executing the Migration Smoothly
To successfully transition to enhanced authentication in Snowflake, you should treat the transition as a structured migration rather than a single config change. The idea is to maintain operational continuity while introducing new security improvements, which should minimize potential disruptions.
The first step of this process is to adopt a phased rollout strategy. Start by enabling MFA or SSO for a small pilot group of users, preferably those with lower-risk roles or teams that can provide detailed feedback on the experience.
This controlled testing phase helps identify any compatibility issues with scripts, integrations, or user workflows. Once these issues are resolved, you can expand the rollout to additional groups in stages until the transition is complete.
User communication and training are critical during this phase, as authentication changes often cause confusion or resistance if users aren’t properly informed about what’s happening and why. Clear, proactive communication in the form of FAQs, step-by-step guides, and brief training sessions ensures users understand how the new system works and how to use it.
Testing and validation are equally important. Thus, you should verify that all user accounts, automated pipelines, and third-party apps can authenticate under the new method before fully deprecating password-only logins. Running controlled tests in staging environments, if available, will help confirm that everything functions as expected.
It’s also a good idea to create a rollback and a contingency plan, just in case something goes south during migration. While seamless migration is the goal, it’s always a good idea to prepare for any unexpected issues that might arise from misconfigured identity provider settings or user lockout.
Finally, proactive monitoring is really important post-rollout. Use Snowflake’s access logs and your identity provider’s audit tools to track login attempts, authentication failures, and anomalies. A sudden increase in failed logins or lockouts often signals misaligned role mapping or incorrect group assignments. It’s also a good idea to set up alerts and reporting mechanisms.
Best Practices and How to Avoid Downtime During Migration
Preventing downtime during authentication migrations starts with careful planning and clear visibility into all Snowflake dependencies, so map every user, pipeline, and 3rd party integration that relies on Snowflake authentication.
It’s really important to roll out in stages, so enable your authentication method for pilot groups first, gather feedback, and resolve any issues before expanding to production. The phased approach reduces risk and ensures mission-critical processes remain unaffected.
When it comes to best practices, start by applying the principle of least privilege, which ensures that users only have access necessary to perform their roles. Make sure to review and audit access permissions to prevent privilege creep over time.
Security is also a people challenge, and teams need ongoing education around safe login practices, phishing awareness, and proper handling of authentication tokens or security keys. With all of this, combined with pre-planning, phased deployment, and real-time monitoring, organizations can migrate to Snowflake secure login with confidence and, most importantly, without costly interruptions.
Conclusion
Deprecation of password-only authentication isn’t just a technical requirement, but a strategic opportunity to modernize and optimize your Snowflake security framework. If your organization needs expert guidance navigating these changes, Data Sleek is ready to help. Explore our Snowflake consulting services today to ensure your authentication strategy is future-proof.


